Analysis: Upbit may have been infiltrated by advanced persistent threat organizations for a long time
PANews reported on November 28 that security firm GoPlus analyzed the recent Upbit attack and pointed out several serious issues: the hot wallet leak indicates vulnerabilities in key management and security risks within the internal network. The cold wallet remains secure. Noteworthy aspects of this incident include: 1. "Anniversary attack"—the attack occurred on the same day as the $50 million hack six years ago in 2019; 2. Well-timed execution—the attack was launched just hours after the major merger announcement between Dunamu and Naver; 3. Typical characteristics of the Lazarus group—attack speed, methods, and symbolic significance; 4. Complex money laundering techniques—using multiple DEX routes, possibly to evade regulation (2,200 SOL tokens were transferred to Binance). All signs suggest that the platform may have been subject to long-term infiltration by an advanced persistent threat (APT) group.
Previously, Upbit disclosed that approximately 54 billion KRW worth of Solana network assets had been stolen; South Korean authorities suspect that the North Korean hacker group Lazarus is behind this attack.
Disclaimer: The content of this article solely reflects the author's opinion and does not represent the platform in any capacity. This article is not intended to serve as a reference for making investment decisions.
You may also like
Ethereum Privacy’s HTTPS Moment: From Defensive Tool to Default Infrastructure
Summarizing the "holistic reconstruction of the privacy paradigm" from dozens of speeches and discussions at the Devconnect ARG 2025 "Ethereum Privacy Stack" event.

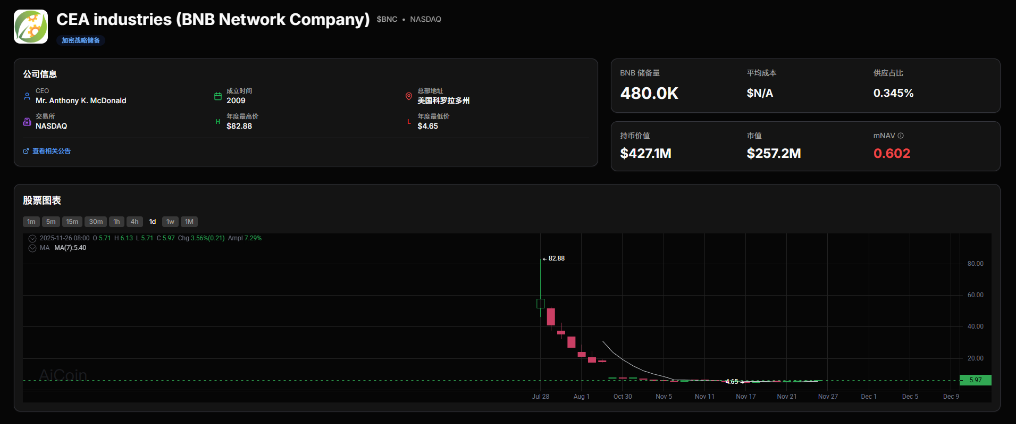
Shareholder Revolt: YZi Labs Forces BNC Boardroom Showdown
Halving Is No Longer the Main Theme: ETF Is Rewriting the Bitcoin Bull Market Cycle

The Crypto Market Amid Liquidity Drought: The Dual Test of ETFs and Leverage

