How a cyberattack operation focused on prominent Gmail and WhatsApp users throughout the Middle East
Phishing Campaign Targets Iranian Activists Amid Internet Blackout
On Tuesday, Iranian activist Nariman Gharib, who is based in the UK, posted on Twitter about receiving a phishing link through WhatsApp. He shared censored screenshots of the suspicious message and cautioned others to avoid clicking on unknown links. Gharib, who monitors digital threats related to Iranian protests, noted that the phishing attempt was aimed at individuals involved in Iran-related activities, including himself.
This cyberattack comes at a time when Iran is experiencing an unprecedented nationwide internet shutdown amid ongoing anti-government demonstrations and harsh crackdowns. With Iran and its adversaries frequently engaging in cyber operations, the incident raised concerns about digital security for those connected to the protests.
After his initial post, Gharib provided TechCrunch with the full phishing link, enabling the team to obtain the source code of the malicious website. He also published a detailed report of his findings.
TechCrunch’s analysis, supported by cybersecurity experts, revealed that the campaign was designed to steal Gmail and other online account credentials, hijack WhatsApp accounts, and gather sensitive data such as location, photos, and audio recordings from victims’ devices.
The true identity of the attackers remains uncertain—they could be state-sponsored operatives, spies, or cybercriminals, or possibly a combination of all three.
During the investigation, TechCrunch discovered a vulnerability that allowed real-time access to victims’ responses stored on the attacker’s server, which was left unprotected. This exposed data showed that dozens of individuals had unknowingly submitted their credentials and were likely compromised.
The victims included a Middle Eastern scholar specializing in national security, the head of an Israeli drone company, a senior Lebanese government official, at least one journalist, and several people in the United States or with American phone numbers.
TechCrunch is sharing these findings after independently verifying much of Gharib’s research. The phishing website has since been taken offline.
How the Attack Unfolded
According to Gharib, the phishing attempt began with a WhatsApp message containing a suspicious link, which directed victims to a fraudulent website.
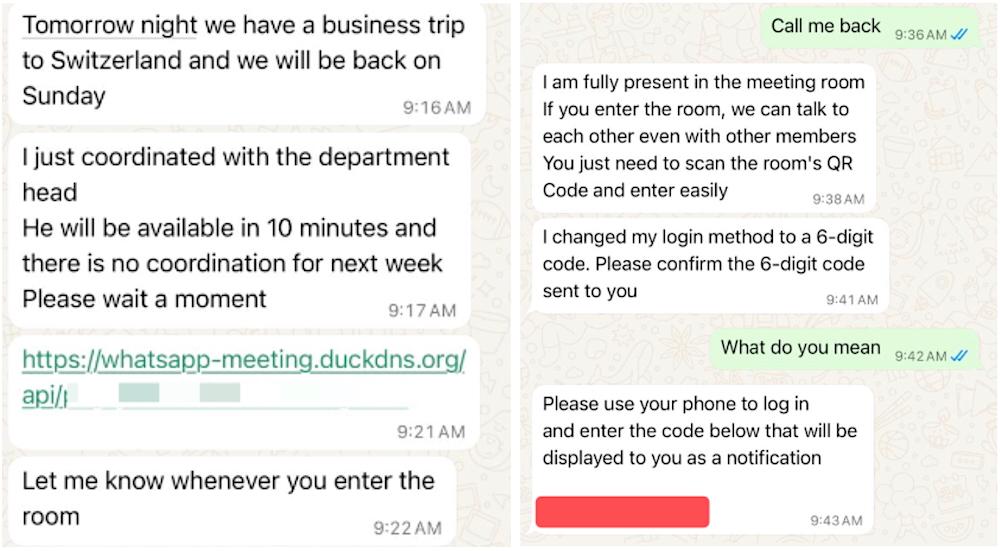
Image Credits: Nariman Gharib
The attackers utilized a dynamic DNS service, DuckDNS, to host their phishing campaign. Such services allow users to assign memorable web addresses—like a duckdns.org subdomain—to servers with changing IP addresses, making it easier to disguise malicious sites.
It remains unclear whether the phishing site was voluntarily taken down by the attackers or disabled by DuckDNS. When contacted, DuckDNS’s owner, Richard Harper, suggested submitting an abuse report.
By using DuckDNS, the attackers could obscure the true location of the phishing page, making it appear more legitimate—such as mimicking an official WhatsApp link.
The actual phishing site was hosted at alex-fabow.online, a domain registered in early November 2025. Several related domains, including meet-safe.online and whats-login.online, were also found on the same server, indicating a broader campaign targeting users of virtual meeting platforms.
The exact mechanism by which the DuckDNS link redirected victims to specific phishing pages is unknown. It’s possible the link customized the destination based on device information.
TechCrunch was unable to interact directly with the phishing page, but reviewing its source code provided insight into the attack’s methods.
Phishing for Gmail Credentials and Phone Numbers
Depending on the target, clicking the phishing link would either display a fake Gmail login page or prompt for a phone number, initiating a process to steal passwords and two-factor authentication codes.
However, the phishing site’s code had a critical flaw: by altering the URL, TechCrunch could access a file on the attacker’s server that logged every victim’s submitted information.
This file contained over 850 entries, documenting each stage of the phishing process for every victim. The records included usernames, passwords, incorrect login attempts, and two-factor codes—essentially functioning as a keylogger.
Additionally, each entry recorded the victim’s user-agent, revealing the operating system and browser used. The campaign targeted users on Windows, macOS, iOS, and Android devices.
The exposed file allowed a step-by-step reconstruction of the attack for individual victims. In one instance, a victim repeatedly entered their email credentials on a fake Gmail page until the correct password was accepted, followed by submission of a two-factor authentication code (typically in the format G-xxxxxx).
Hijacking WhatsApp and Extracting Browser Data
Beyond stealing login credentials, the campaign also sought to access victims’ locations, photos, and audio by tricking them into granting permissions.
In Gharib’s case, clicking the phishing link opened a counterfeit WhatsApp-themed page displaying a QR code. The ruse was designed to convince the target to scan the code, supposedly to join a virtual meeting.
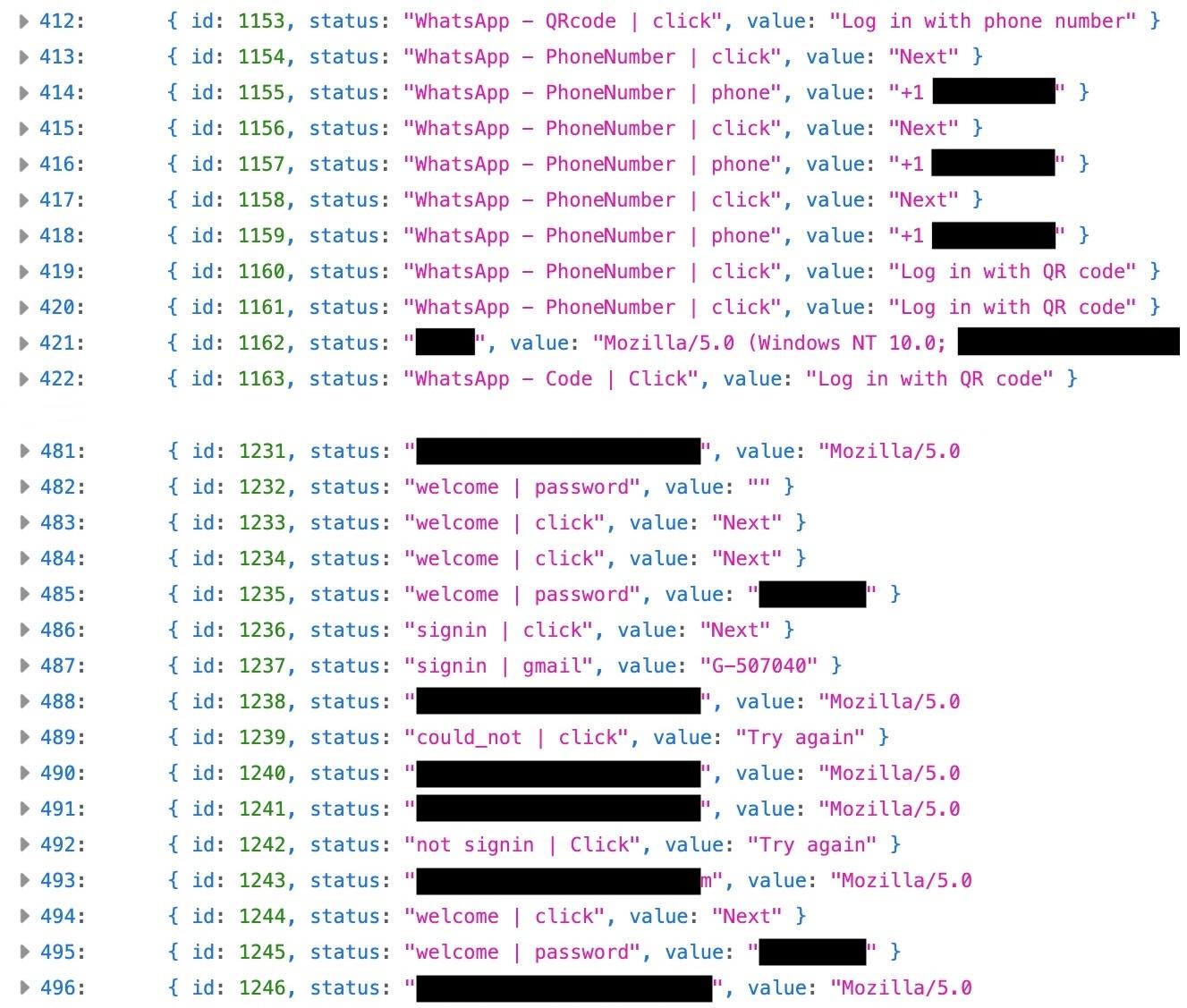
Image Credits: TechCrunch
Gharib explained that the QR code was generated by the attacker, and scanning it would immediately link the victim’s WhatsApp account to a device controlled by the attacker, granting them access to private data. This technique exploits WhatsApp’s device linking feature, which has also been used to compromise users of other messaging apps like Signal.
Security expert Runa Sandvik examined the phishing page’s code and found that it prompted users to grant access to their location (via navigator.geolocation), as well as photos and audio (using navigator.getUserMedia).
If the victim approved these requests, their coordinates would be sent to the attacker in real time, with updates every few seconds as long as the page remained open. The code also enabled the attacker to record short audio clips and take photos every few seconds using the device’s camera. However, no evidence was found that such data had been stored on the attacker’s server.
Victims, Motives, and Attribution
The individuals behind this campaign remain unidentified. What is certain is that the operation succeeded in stealing credentials from a number of victims, and similar attacks could occur again in the future.
Although some targeted individuals have been identified, there is insufficient information to fully understand the campaign’s scope. The number of confirmed victims is relatively small—fewer than 50—but includes a diverse group: members of the Kurdish community, academics, government officials, business leaders, and other influential figures across the Iranian diaspora and the Middle East.
It is possible that many more people were affected, which could shed light on the attackers’ selection criteria and objectives.
Could This Be State-Sponsored Espionage?
The motivation behind the theft of credentials and WhatsApp accounts is unclear, but such actions could help identify the perpetrators.
A government-backed group might seek access to the email accounts and two-factor codes of high-profile targets—such as politicians or journalists—to obtain confidential information.
This theory is plausible given Iran’s current isolation from the global internet, making information gathering challenging. Both Iranian authorities and foreign governments with interests in Iran could have reasons to monitor communications among influential individuals connected to Iran.
The timing and choice of targets suggest the possibility of an espionage operation focused on a select group of people.
Security researcher Gary Miller from Citizen Lab, who specializes in mobile espionage, reviewed the phishing code and some of the exposed data. He noted that the attack bore the hallmarks of a spearphishing campaign linked to Iran’s Islamic Revolutionary Guard Corps (IRGC), citing the international range of victims, credential theft, abuse of messaging platforms, and use of social engineering tactics.
Financially Motivated Cybercrime?
Alternatively, a financially driven hacker could use stolen Gmail credentials and two-factor codes to access sensitive business information or drain cryptocurrency and bank accounts by resetting passwords.
However, the campaign’s emphasis on collecting location and media files is atypical for financially motivated attackers, who usually have little interest in such data.
Threat researcher Ian Campbell from DomainTools analyzed the campaign’s domains and found that most were registered in early November 2025, with one dating back to August 2025. He described the domains as medium-to-high risk and suggested they were likely part of a financially motivated cybercrime operation.
It’s worth noting that the Iranian government has previously outsourced cyberattacks to criminal groups to obscure its involvement. The U.S. Treasury has sanctioned Iranian companies for acting as fronts for the IRGC and conducting phishing and social engineering attacks.
As Miller emphasized, “Clicking on unsolicited WhatsApp links, no matter how convincing they appear, is extremely risky and should be avoided.”
Disclaimer: The content of this article solely reflects the author's opinion and does not represent the platform in any capacity. This article is not intended to serve as a reference for making investment decisions.
You may also like
XRP Confirms First Golden Cross of 2026, and Bulls Are Already Targeting 13% Upside
XRP vs Ethereum: Can XRP Catch Up by 2030?
One Year of $TRUMP: The Meme Coin That Shook Crypto
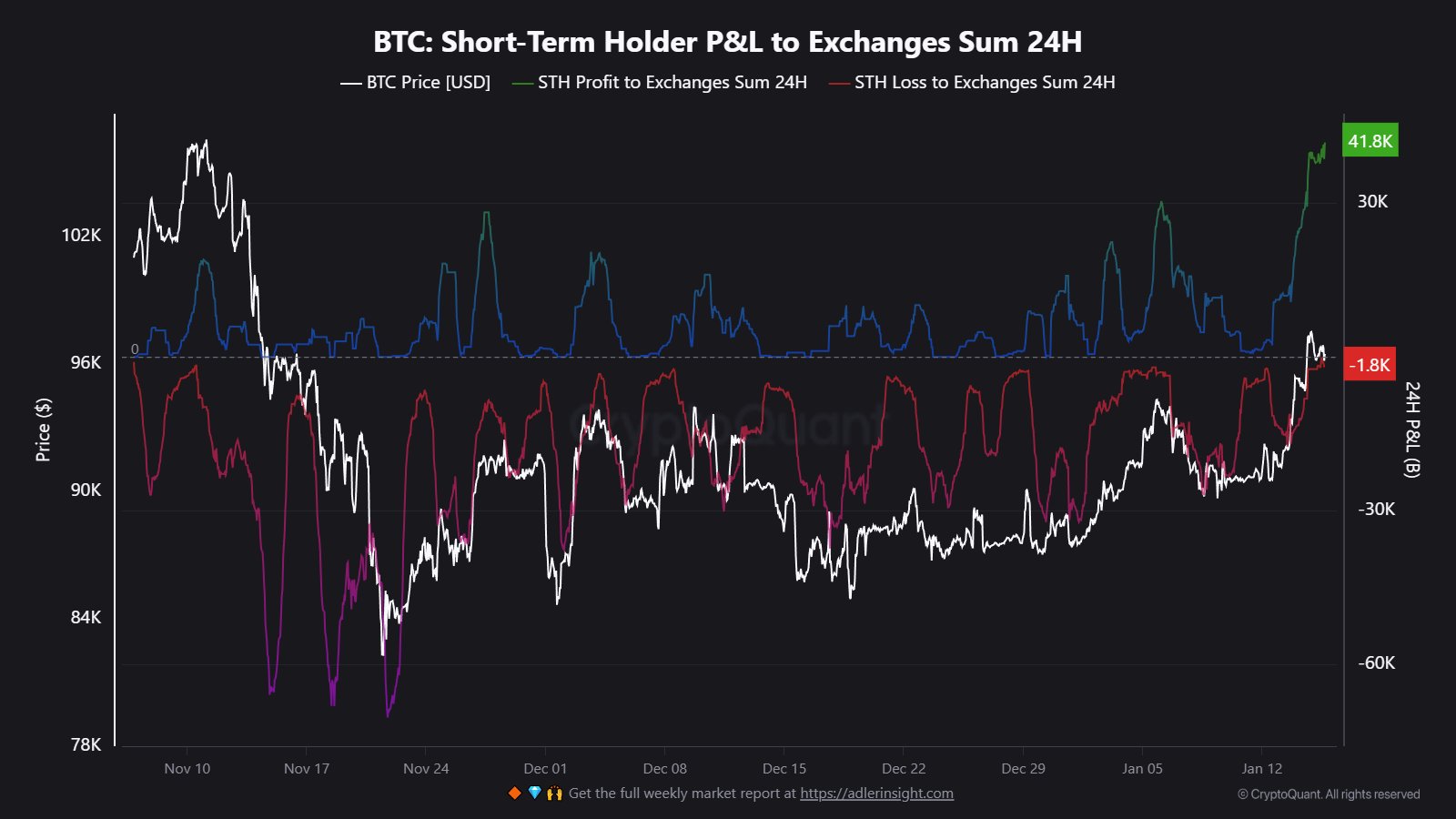
Bitcoin Short-Term Holders Take Profits: 41,800 BTC Sent To Exchanges